Encyclopedia
A
Antivirus Software
Antivirus software acts as a digital bodyguard, protecting your computer system from malicious software (malware) such as viruses, worms, and Trojans. It works by scanning files and programs for known malware signatures and suspicious behavior, alerting you to potential threats and often offering options to remove or quarantine them. Think of it as a security guard at a concert venue, scanning tickets and checking for suspicious packages to keep the bad guys out.
API
API stands for Application Programming Interface. It's a set of rules and specifications that define how two pieces of software can interact with each other. It's like a messenger or translator that enables different applications to communicate and exchange data with each other, even if they're written in different programming languages or run on different platforms.
Here’s the gist of how they work:
The client software makes requests to APIs, asking for specific data or actions and providing the necessary information.
APIs process requests and return responses: They communicate with the other application's backend systems, fetch the requested data or perform the actions, and deliver the results back to the client application.
This exchange happens seamlessly: Applications don't need to know the internal workings of the API or the backend systems, just like you don't need to know how the kitchen at a restaurant works to order food.
APIs play a crucial role in the modern digital landscape, enabling the seamless communication and exchange of data between different applications and services. They are essential for building innovative, interconnected, and user-friendly digital experiences.
Why APIs Are Important:
Integration: Connect different applications and services, creating seamless user experiences and data flows.
Functionality: Access third-party services and data without needing to build everything from scratch.
Innovation: Build new applications and services on top of existing platforms and data.
Scalability: Allow for easy expansion and updates without disrupting existing systems.
Standardization: Promote consistent communication between different systems.
Watch the video to learn more about APIs and how they work!
Examples of APIs in Action:
Weather apps: Use weather APIs to retrieve real-time weather data from providers.
Social media apps: Integrate with social media APIs to allow users to share content and connect with friends.
Maps apps: Rely on map APIs to display maps and provide directions.
Payment apps: Connect with payment APIs to process transactions securely.
E-commerce platforms: Use APIs to connect with payment gateways, shipping providers, and inventory systems.
App (application)
An "app" , which is short for application is a software program designed to perform a specific function. Your web browser for searching, email, social media accounts, what you use to create and edit documents on a computer or mobile device, even the button you press to make video or phone calls on your smartphone are all apps. Apps have built in code to make your computing device follow a command without you having to write the code for each command or task you want the device to perform. Computers as we know them today would be much more complicated to use without application software.
AR
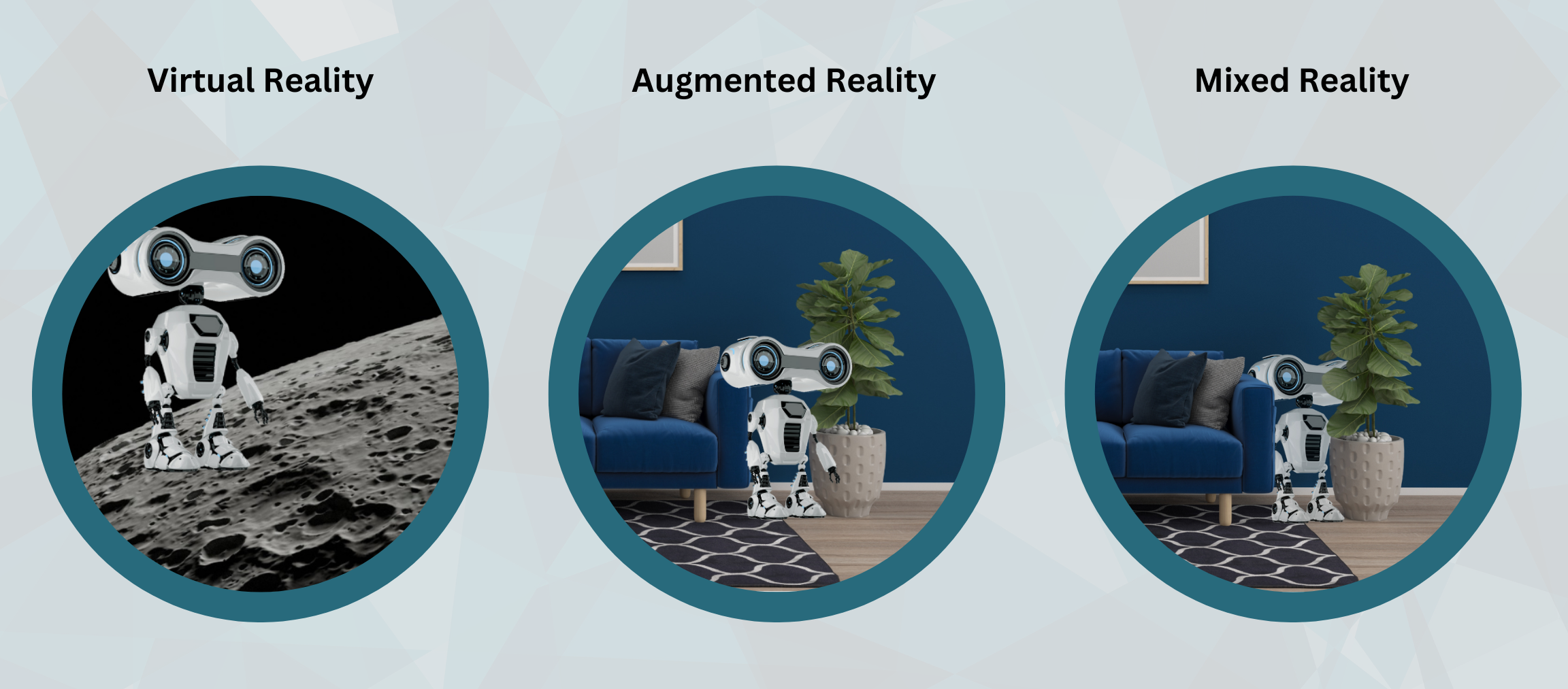
AR stands for augmented reality. AR takes computer generated content and overlays it onto what you also see in the real world. Filters people love to use on social media apps are a great example of augmented reality. The actual environment and/or body of an object or person remains while a variation of color or a virtual picture of an object is laid on top. AR is different than VR or "virtual reality" where the entire environment is computer generated and most or all of the real world is shut out. This is usually done with VR googles where AR is usually experienced via a phone camera. Another variation of AR is MR, or mixed reality, when computer generated content is integrated and interacts with the real world as opposed to simply being like a filter laid on top of it.
B
Biometrics
Biometrics involve using unique physical or behavioral characteristics, like fingerprints, iris scans, or voice recognition, for authentication and identification. It offers a more secure alternative to traditional passwords, as these biological traits are difficult to forge or steal. Imagine unlocking your phone with your fingerprint instead of a password, adding an extra layer of security that's unique to you.

Blockchain
Imagine a ledger, but one that's not just accessible to one person or institution, but distributed across a network of computers. That's essentially what a blockchain is: a shared digital ledger that records transactions in a secure and transparent way. Each transaction is added as a block, linked to the previous ones, creating a chain of verifiable information. Blockchain technology powers cryptocurrencies like Bitcoin but also has broader applications in areas like supply chain management and digital voting.
Botnet
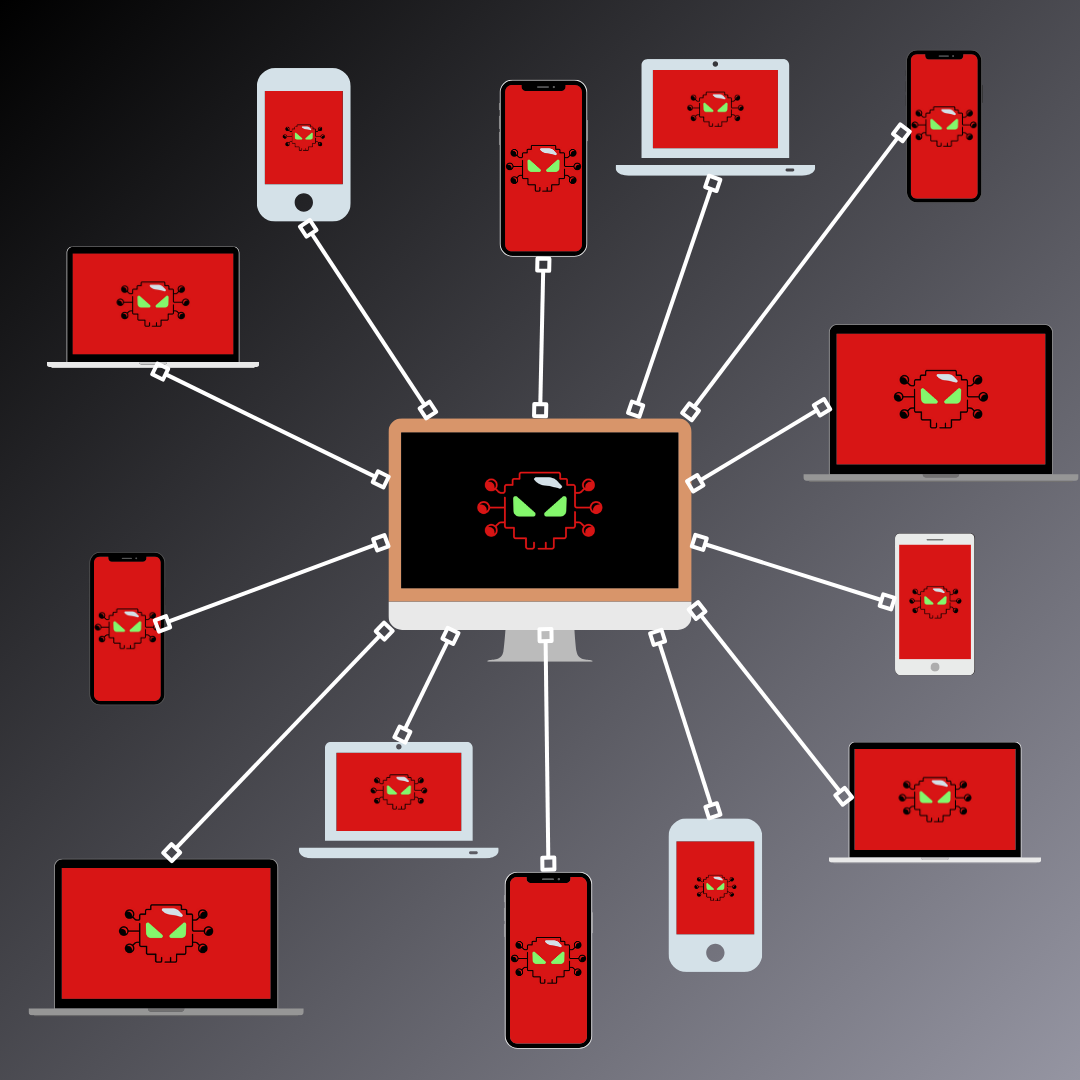
A botnet is a network of compromised computers, also known as "bots," controlled by a central attacker. These bots can be used for various malicious activities, such as launching DDoS attacks, sending spam, or stealing data. Imagine a puppet master pulling the strings of an army of marionettes, each one following commands and potentially causing harm.
C
Cloud Computing
Cloud computing describes the delivery of on-demand computing services, like servers, storage, databases, and software, over the internet. It's like renting a virtual office space instead of building your own building. Users can access these services on demand, scaling them up or down as needed, without the burden of maintaining physical infrastructure.
Watch the video to learn more about cloud computing and how it works!
Code
Computer code is also referred to as "source code" at times. It is the programming language used to create computer programs and the algorithms they use as a set of rules to tell them what actions to perform. Code is used to build apps, (see app), as well as program articifical intelligence for all kinds of computing devices.
The most commonly known types of coding language include: JavaScript, Python, HTML/CSS, and SQL. These are used for multiple purposes, from web development to data analysis to machine learning.
Cookies
In a computer context, cookies are small pieces of data that websites store on your device when you visit them. They act like little reminders, helping websites remember your preferences and actions, making your subsequent visits smoother and more personalized.
Here's how they work
Cookie Creation: When you visit a website, it may send a cookie to your browser, which stores it on your device.
Information Storage: Cookies can contain various types of information, such as:
Login details (username, email) to keep you logged in
Site preferences (language, theme) to tailor your experience
Shopping cart items to remember what you want to buy
Tracking information to monitor your browsing behavior
Cookie Retrieval: When you revisit the same website, your browser sends the stored cookie back to the website.
Personalized Experience: The website reads the cookie and uses the information to:
Keep you logged in
Display your preferred settings
Remind you of items in your cart
Show you relevant ads or content
Types of Cookies
Session Cookies: Temporary cookies that expire when you close your browser. They are often used to maintain active sessions and store temporary information.
Persistent Cookies: Remain on your device even after you close your browser and have a specified expiration date. They are used to store preferences and track user behavior over time.
First-Party Cookies: Created by the website you are visiting and can only be read by that website.
Third-Party Cookies: Created by websites other than the one you are visiting, often used for tracking and advertising purposes.
Common Uses of Cookies:
Personalization: Tailoring website content and features to individual users' preferences.
Shopping Carts: Keeping track of items added to a shopping cart during an online shopping session.
Login Information: Maintaining user sessions and preventing the need for repeated logins.
Tracking and Analytics: Collecting data about user behavior to understand website usage and improve performance.
Advertising: Targeting ads based on user interests and browsing history
Watch the video to learn more about cookies and how they work!
Managing your cookies
You may have also heard about privacy concerns with cookies. Tracking cookies can be used to track users' online activity across multiple websites, raising privacy concerns about data collected on consumers. Third-party cookies can be particularly concerning as they can collect data without users' explicit knowledge or consent.
Most browsers allow you to view, manage, and delete cookies. You can access these options via your browser settings. Most web browsers also offer you privacy tools such as extensions and add-ons that can help block or manage cookies more effectively. Browsing in "Incognito" or "Private" mode prevents cookies from being stored during a browsing session.
It's essential to be aware of cookies, their purposes, and how to manage them to protect your privacy while enjoying a personalized online experience.
Cryptocurrency
A cryptocurrency, often shortened to "crypto," is a digital or virtual currency secured by cryptography, making it difficult to counterfeit or double-spend. Cryptocurrency appeals to many users because unlike traditional currency issued by central banks, cryptocurrencies operate on decentralized networks, typically utilizing blockchain technology. These networks allow for peer-to-peer transactions without the need for intermediaries like banks or financial institutions.
Key Features
Decentralization: No single entity controls the issuance or maintenance of the currency. Transactions are verified and recorded on a distributed ledger (blockchain) accessible to all network participants.
Cryptography: Advanced encryption techniques secure transactions and protect user identities.
Immutability: Once recorded on the blockchain, transactions cannot be altered or reversed.
Pseudonymity: Users can participate without revealing their real identities, although transactions are publicly viewable on the blockchain.
Scarcity: Many cryptocurrencies have a predetermined maximum supply, limiting inflation and potentially increasing value over time.
Applications
Digital payments: Used for online and offline transactions, bypassing traditional financial systems.
Investment: Traded on cryptocurrency exchanges as speculative assets, with prices experiencing significant volatility.
Decentralized finance (DeFi): Enables peer-to-peer lending, borrowing, and financial services without intermediaries.
Non-fungible tokens (NFTs): Represent unique digital assets like artwork or collectibles on the blockchain.
Supply chain management: Track and verify the movement of goods and materials through secure blockchain records.
Types of Cryptocurrencies
Bitcoin: The first and most well-known cryptocurrency, often considered the "digital gold" due to its limited supply and perceived store of value.
Ethereum: A programmable blockchain platform that supports not only its own cryptocurrency (Ether) but also the development of decentralized applications (dApps).
Stablecoins: Cryptocurrencies pegged to the value of another asset, such as the US dollar, to offer price stability for transactions and investments.
Altcoins: Any cryptocurrency other than Bitcoin, encompassing a diverse range of projects with varying functions and technologies.
Beware exploring options outside of Bitcoin and Ethereum which have been rife with scamming and pump and dump schemes, especially by online influencers.
Challenges and Controversies
Volatility: Cryptocurrency prices can fluctuate dramatically, posing risks for investors and hindering widespread adoption as a medium of exchange.
Energy consumption: Some cryptocurrencies, like Bitcoin, require significant energy for mining, raising environmental concerns.
Regulation: Uncertain and evolving regulatory landscapes may impede the growth and legitimacy of the cryptocurrency industry.
Security: Cryptocurrency exchanges and wallets can be vulnerable to hacking and theft, requiring users to take robust security measures.
Illegal activities: Cryptocurrency has been used in some illegal activities like money laundering and ransomware attacks.
Future Outlook
Cryptocurrency is a rapidly evolving technology with the potential to revolutionize various aspects of the financial system and beyond. Despite its challenges, cryptocurrency adoption and innovation are likely to continue, shaping the future of decentralized finance and digital transactions. The federal government is behind, but catching up on regulating this asset. This is a highly volatile type of asset that is more akin to gambling than investing, even today. Buyer beware.
Cybersecurity
Cybersecurity encompasses the practices, technologies, and tools used to protect computer systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It's like building a digital fortress around your valuable information, using various defensive measures to keep out intruders and keep your data safe.
D
Dark Web
Imagine a hidden corner of the internet accessible only through special software, like a secret room behind a bookcase. That's the dark web, where anonymity reigns and illegal activities often flourish. While some legitimate uses exist, the dark web's unregulated nature makes it a breeding ground for cybercrime and other illicit activities.
Data Breach
When sensitive information like personal data, financial records, or medical records is accessed or stolen without authorization, it's called a data breach. These breaches can have significant consequences for individuals and organizations, highlighting the importance of data security and responsible data handling.
Decryption
Encryption scrambles information into a secret code, while decryption reverses the process, unlocking the code and revealing the original message. Think of it like a treasure map with coded directions; decryption is the key that translates the code and leads you to the buried treasure.
DDoS (Distributed Denial-of-Service) Attack
Imagine a crowd flooding a restaurant, overwhelming the staff and preventing other customers from entering. That's essentially what a DDoS attack does; it floods a website or server with traffic, making it unavailable to legitimate users. These attacks can disrupt businesses, compromise data, and damage online reputations. A DDoS attack is carried out by a network of computers and other internet devices usually infected with malware that allows them to be remotely controlled by an attacker. (see botnet) Sometimes these attacks are the precursor of a nother more malicious attack to follow. It is important to keep website and network security updated to help prevent these kind of attacks from happening.
Domain Name
A domain name is a unique, human-readable name that identifies a website or other internet resource. It serves as an address that people can easily remember and type into their web browsers to access specific websites or online services. It's like a street address for a house, but instead of identifying a physical location, it points to a virtual location on the internet.
Key Components
Top-Level Domain (TLD): The part of the domain name that comes after the dot, such as .com, .org, .net, .edu, .gov, etc. TLDs categorize websites by their purpose or affiliation.
Second-Level Domain (SLD): The main part of the domain name, typically the name of the website or organization, such as "google" in "google.com" or "wikipedia" in "wikipedia.org."
Subdomains (Optional): Additional levels of hierarchy within a domain, such as "www" in "www.google.com" or "en" in "en.wikipedia.org."
How Domain Names Work
Domain Name Registration: To obtain a domain name, individuals or organizations register it through a domain name registrar.
Domain Name System (DNS): When you enter a domain name into a web browser, the DNS translates it into the corresponding IP address, which is a numerical address that computers use to communicate with each other.
Website Access: The browser then uses the IP address to locate and connect to the web server that hosts the website's content.
Purposes of Domain Names
Branding and Identity: Domain names create a recognizable online presence for businesses, organizations, and individuals.
Website Accessibility: They make it easy for people to find and access websites.
Email Communication: Domain names are used for email addresses, providing a professional and consistent way to communicate online.
Online Marketing: They play a crucial role in search engine optimization (SEO) and online marketing strategies.
Additional Information
Domain names can be purchased or leased for a period of time. They can be transferred between owners. It's essential to choose a domain name that is relevant, memorable, and easy to type. Domain names can be valuable assets for businesses and organizations.
DNS (Domain Name System)
The Domain Name System (DNS) is the internet's phonebook. It's a hierarchical and distributed naming system that translates human-readable domain names (like www.example.com) into machine-readable IP addresses (like 192.168.1.1). This makes it possible for people to navigate the internet using easy-to-remember names, rather than having to memorize a long string of numbers for every website they want to visit.
How It Works
User Request: When you type a domain name into your web browser, your device first checks its local DNS cache to see if it has a record of the corresponding IP address. If it doesn't, it sends a DNS query to a DNS server.
DNS Lookup: The DNS server, which is typically operated by your internet service provider (ISP), then starts a process called DNS resolution. It queries a series of authoritative DNS servers, each responsible for a specific part of the domain name hierarchy, to find the correct IP address.
Response: Once the correct IP address is found, the DNS server sends it back to your device. Your device can then use this IP address to connect to the website.
Cache: The IP address is also stored in your device's local DNS cache for a period of time, so that future requests for the same domain name can be resolved more quickly.
Key Components
DNS Servers: Computers that store and manage DNS records.
Domain Names: Human-readable names for websites and other internet resources.
IP Addresses: Unique numerical addresses assigned to devices on the internet.
DNS Records: Information that maps domain names to IP addresses.
DNS Resolvers: Software that translates domain names into IP addresses.
Digital Forensics
Digital forensics is the branch of forensic science that deals with the gathering, preservation, analysis, and presentation of digital evidence. This evidence can be found on a variety of devices, including computers, mobile devices, hard drives, flash drives, routers, firewalls, even cameras, drones, and wearable tech.
The primary goal of digital forensics is to recover and analyze digital evidence in a way that is admissible in court, meaning it can be used as evidence in legal proceedings. This requires careful adherence to established practices and procedures to ensure the integrity of the evidence and prevent tampering.
Applications of digital forensics
Law enforcement: Investigating cybercrime, computer fraud, sexual content involving minor children, and other criminal activities.
Civil litigation: Supporting legal cases involving intellectual property, data breaches, and contract disputes.
Corporate investigations: Investigating internal fraud, employee misconduct, and data breaches.
Incident response: Responding to security incidents involving malware, hacking, and data breaches.
Digital forensics is a complex and specialized field that requires a deep understanding of technology, legal procedures, and investigative techniques. Professionals in this field often have backgrounds in computer science, law enforcement, or forensics.
DNS Hijacking (Domain Name System Hijacking)
DNS hijacking, also known as DNS redirection or DNS poisoning, is a type of cyberattack that disrupts the normal Domain Name System (DNS) resolution process to redirect users to malicious or unintended websites. It's a serious threat that can lead to credential theft, malware infections, data loss, and other harmful consequences.
How It Works
Attacker Compromises DNS: The attacker gains control over a DNS server or manipulates DNS settings on a user's device or router.
User Requests Website: The user attempts to visit a website by entering its domain name into a web browser.
Rogue DNS Server: Instead of resolving the domain name correctly, the compromised or manipulated DNS server directs the user to a rogue server controlled by the attacker.
Malicious Redirection: The rogue server sends the user to a malicious website that may look legitimate but is designed to steal information, install malware, or carry out other harmful actions.
Common Methods
Malware Infection: Attackers often use malware to change DNS settings on a user's device without their knowledge.
Router Attacks: Vulnerabilities in routers can be exploited to modify DNS settings and redirect traffic.
DNS Spoofing: Attackers can intercept legitimate DNS responses and forge fake responses to redirect users.
ISP DNS Hijacking: Some internet service providers (ISPs) may intentionally redirect users to their own servers for advertising or tracking purposes.
Risks and Consequences
Phishing Attacks: Attackers can use DNS hijacking to direct users to fake websites that mimic legitimate ones, tricking them into entering sensitive information like login credentials or financial details.
Malware Distribution: Malicious websites can install malware on a user's device, leading to further infections and data breaches.
Data Theft: Attackers can collect sensitive data such as browsing history, passwords, and financial information.
Censorship: Governments or organizations can use DNS hijacking to block access to certain websites or content.
Prevention and Protection
Use Strong Passwords: Protect your router and devices with strong, unique passwords to prevent unauthorized access.
Keep Software Updated: Regularly update your operating system, browsers, and security software to address vulnerabilities.
Use a Trusted DNS Provider: Consider using a reputable third-party DNS provider known for security and privacy.
Install a VPN: Encrypt your internet traffic with a virtual private network (VPN) to protect against DNS hijacking.
Be Cautious Online: Be wary of suspicious links and emails, and only visit websites with a secure HTTPS connection.
Check DNS Settings: Regularly check your DNS settings to ensure they haven't been tampered with.
Use DNS Security Features: Some security software and routers offer DNS security features that can help detect and prevent DNS hijacking attempts.
E
Encryption
Encryption is the process of encoding information in a way that only authorized parties can access and understand it. It's like putting a lock on your data, where only those with the key can unlock it. This protects sensitive information from unauthorized access, theft, or alteration, ensuring confidentiality and integrity.
How It Works
Plaintext to Ciphertext: The original, readable message or data is called plaintext. Encryption uses a mathematical algorithm called a cipher to transform the plaintext into an unreadable, scrambled format called ciphertext.
Encryption Key: The encryption process relies on a key, which is a secret piece of information that controls the scrambling and unscrambling of the data. The strength of the encryption depends on the complexity of the key.
Decryption: To reverse the process and reveal the original plaintext, the authorized recipient uses a decryption key, which is typically the same as or mathematically related to the encryption key.
Types of Encryption
Symmetric Encryption: Uses the same key for both encryption and decryption. It's fast and efficient but requires secure key exchange between parties.
Asymmetric Encryption: Uses two different keys (public key and private key). The public key can be shared widely for encryption, while the private key is kept secret for decryption. It's slower than symmetric encryption but offers more secure key exchange.
Hashing: A one-way encryption function that converts data into a unique, fixed-length string called a hash. It's often used for password storage and integrity verification, as it's impossible to reverse the hash to retrieve the original data.
Common Uses of Encryption
Secure Communication: Protecting online communication like emails, messaging, and voice calls.
Data Protection: Securing sensitive data stored on computers, servers, and mobile devices.
Financial Transactions: Protecting online banking, credit card transactions, and financial information.
Password Security: Storing passwords securely in databases and systems.
File Protection: Encrypting files and folders to prevent unauthorized access.
Digital Signatures: Verifying the authenticity and integrity of digital documents and messages.
Virtual Private Networks (VPNs): Creating secure, encrypted connections over public networks.
Benefits of Encryption
Confidentiality: Protects sensitive information from unauthorized access.
Integrity: Ensures that data remains unaltered during transmission or storage.
Authentication: Verifies the identity of senders and recipients.
Non-repudiation: Provides proof of origin and prevents senders from denying they sent a message.
Compliance: Helps organizations meet data privacy and security regulations.
F
Firewall
A firewall is a security system that monitors and controls incoming and outgoing network traffic. It acts as a barrier between a trusted internal network (such as a private computer or local network) and an untrusted external network (such as the internet), to protect against unauthorized access, malicious attacks, and data breaches.
Key Functions
Packet Filtering: Inspects individual data packets (small units of network traffic) and decides whether to allow or block them based on predefined rules, such as source and destination IP addresses, port numbers, and protocols.
Stateful Inspection: Keeps track of the state of network connections to allow legitimate traffic to flow while blocking unwanted or suspicious connections.
Application Control: Restricts access to specific applications or services, preventing unauthorized or potentially harmful programs from running.
Intrusion Detection and Prevention: Monitors network traffic for signs of attacks and attempts to block them in real-time.
Types of Firewalls
Hardware Firewalls: Dedicated physical devices that are typically positioned between a network and the internet.
Software Firewalls: Software programs installed on individual computers or servers.
Cloud-Based Firewalls: Firewall services provided by cloud-based security providers.
Common Features
Access Control Lists (ACLs): Define permitted and denied traffic based on specific criteria.
Port Blocking: Controls access to specific network ports used by different applications or services.
VPN Support: Allows secure remote access to private networks.
Logging and Reporting: Tracks network activity and generates reports for analysis and auditing.
Benefits of Firewalls
Protection against Cyberattacks: Prevents unauthorized access, malware infections, data theft, and other security threats.
Data Security: Protects sensitive information from being compromised.
Network Segmentation: Divides networks into zones to isolate sensitive areas and control traffic flow.
Compliance: Helps organizations meet security regulations and standards.
Enhanced Security: Provides an additional layer of protection beyond basic security measures.
H
Honeypot/trap
In an internet context, a honeypot often takes on a digital form, aiming to deceive and exploit users online.
Common types of honeypots you might encounter
Phishing Traps: These utilize fake websites, emails, or social media profiles designed to resemble legitimate platforms or trusted individuals. By luring users with promises of deals, exclusive content, or even romance, they aim to steal personal information, login credentials, or financial data.
Dating Scam Honeytraps: Fake online dating profiles are employed to attract unsuspecting users, building emotional connections and trust. Once hooked, scammers might pressure victims into sending money, divulging sensitive information, or even visiting them in person for potential harm.
Malicious Links and Downloads: Disguised as seemingly harmless links or files, these traps aim to infect devices with malware once clicked or downloaded. This malware can steal data, spy on user activity, or even hijack systems for nefarious purposes.
Social Media Honeypots: Fake social media accounts, groups, or forums designed to attract specific demographics or target groups with enticing content. By engaging with users and gaining their trust, perpetrators might spread misinformation, manipulate opinions, or harvest personal data for various malicious uses.
Botnet Traps: Attackers might create networks of compromised devices (bots) designed to carry out cyberattacks. They might trick users into interacting with these bots through manipulated online content, allowing the bots to spread malware or launch denial-of-service attacks.
Protecting Yourself from Honeytraps
Be wary of unsolicited offers and messages: Look for inconsistencies, spelling errors, or overly eager promises that seem too good to be true.
Verify links and sources before clicking: Hover over links to see their actual destination and avoid downloading files from untrusted sources.
Maintain strong passwords and practice good cyber hygiene: Use complex passwords for different accounts and be cautious about sharing personal information online.
Beware of emotional manipulation: Scammers often prey on emotions like love, fear, or urgency to manipulate victims. Stay vigilant and skeptical of online relationships that progress too quickly.
Use security software and browser extensions: Invest in reliable antivirus and anti-malware software and consider using anti-spam extensions to filter out suspicious emails and websites.
By staying informed and practicing online safety measures, you can significantly reduce your risk of falling victim to internet honeytraps. Remember, if something seems suspicious or too good to be true, it probably is. Always think before you click or engage, and trust your gut instinct when something feels off.
HTTP vs HTTPS
HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) are two essential protocols that govern how data is exchanged between web browsers and web servers. While they both serve the same fundamental purpose, they differ significantly in terms of security and privacy.
Key Differences and Why It Matters
Encryption:
HTTP: Doesn't encrypt data, meaning information is sent in plain text, vulnerable to interception and eavesdropping.
HTTPS: Secures data using encryption, typically using TLS (Transport Layer Security) or SSL (Secure Sockets Layer). This scrambles the data, making it unreadable to anyone without the decryption key, protecting sensitive information like passwords, credit card numbers, and personal details.
Port Number:
HTTP: Uses port 80 as its default port where information remains plain text and unencrypted between browser and server, and is therefore unsecured. This is why you should not enter any sensitive information into unsecured websites.
HTTPS: Uses port 443 as its default port. Information is encrypted between browser and server.
Security Indicator:
HTTP: Websites using HTTP typically display "http://" in the address bar, without any security indicators.
HTTPS: Websites using HTTPS show "https://" with a padlock icon in the address bar, visually indicating secure communication.
Authentication:
HTTPS: Often uses digital certificates to verify the identity of websites and establish trust, reducing the risk of phishing attacks and fake websites.
Why HTTPS Matters
Security: Protects sensitive information from interception and misuse, crucial for online transactions, banking, and personal data protection.
Privacy: Prevents websites and third parties from tracking your online activity and collecting personal information.
Trust: Indicates a website's commitment to security and trustworthiness, enhancing user confidence.
SEO: Search engines like Google favor HTTPS websites, potentially improving search rankings.
In summary, HTTPS is the more secure and recommended protocol for web browsing. It's essential to use HTTPS whenever possible, especially when handling sensitive information or accessing personal accounts. Check for the "https://" and padlock icon in the address bar to ensure a secure connection.
I
Identity Theft
Identity theft is a crime in which someone steals your personal information, such as your name, Social Security number, credit card numbers, or other identifying details, and uses it without your permission to commit fraud or other crimes. This can have serious financial, emotional, and reputational consequences for victims.
How It Happens
Data Breaches: Hackers break into databases of companies or organizations to steal personal information of large numbers of people.
Phishing Scams: Fake emails or websites designed to trick people into revealing their personal information.
Malware: Malicious software installed on devices to steal data without the victim's knowledge.
Physical Theft: Losing a wallet, purse, or documents containing sensitive information.
Skimming: Criminals use devices to steal credit card information at ATMs or payment terminals.
Social Engineering: Manipulating people into giving up personal information through phone calls, emails, or social media.
Common Types of Identity Theft
Financial Identity Theft: Using stolen information to open new accounts, make unauthorized purchases, apply for loans, or access existing accounts.
Medical Identity Theft: Using stolen information to obtain medical services or prescriptions, fake billing, or create fraudulent medical records.
Government Identity Theft: Using stolen information to file false tax returns, claim benefits, or commit other crimes involving government agencies.
Child Identity Theft: Using a child's information to open accounts or commit fraud.
Effects of Identity Theft
Financial Losses: Unauthorized charges, damaged credit scores, debt collection actions, and difficulty obtaining credit in the future.
Emotional Distress: Stress, anxiety, fear, and feeling violated.
Time and Effort: Resolving issues, contacting creditors, disputing charges, and restoring credit history.
Reputational Damage: False information on credit reports, criminal records, or employment history.
Prevention Tips
Protect Your Personal Information: Be cautious about sharing personal information online or over the phone.
Use Strong Passwords: Create unique and complex passwords for all accounts.
Monitor Your Accounts: Regularly check your credit reports, bank statements, and credit card statements for any unauthorized activity.
Shred Sensitive Documents: Before discarding any documents containing personal information.
Be Cautious Online: Use secure websites, avoid clicking on suspicious links or emails, and be wary of social media scams.
Install Security Software: Protect your devices with antivirus and anti-malware software.
Report Suspected Identity Theft: Immediately contact authorities and financial institutions if you suspect your identity has been compromised.
IP Address (Internet Protocol Address)
An IP address is a unique numerical label assigned to every device connected to a computer network that uses the Internet Protocol for communication. It's like a street address for your device on the internet, allowing other devices to find and communicate with it.
Key Roles
Device Identification: Distinguishes one device from another on a network.
Location Addressing: Specifies the device's location within the network.
Data Routing: Enables the accurate delivery of data packets to their intended destinations.
Types of IP Addresses
IPv4 (Internet Protocol Version 4): The most common type, consisting of four numbers separated by dots, like 192.168.1.100. Each number can range from 0 to 255.
IPv6 (Internet Protocol Version 6): The newer version, designed to address the shortage of IPv4 addresses. It uses a longer, alphanumeric format, like 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
How IP Addresses Work
Assignment: IP addresses are assigned by internet service providers (ISPs), network administrators, or automatically through Dynamic Host Configuration Protocol (DHCP).
Routing: When you send data (like a website request), your device includes its IP address in the data packets.
Delivery: Routers on the network use the IP address to determine the destination and forward the packets accordingly, ensuring they reach the correct device.
Common Examples
Public IP Address: Assigned to your home or office network by your ISP, used for accessing the internet.
Private IP Address: Used within a private network (like your home Wi-Fi) to identify devices locally.
Static IP Address: A fixed address that doesn't change.
Dynamic IP Address: An address that can change periodically.
Additional Information
IP addresses can be used to track your online activity and location.
VPNs (virtual private networks) can mask your IP address for privacy and security.
IP addresses are essential for many internet services like email, web browsing, and online gaming.
K
Keystroke Logging (Keylogging)
Keystroke logging, also known as keylogging or keyboard capturing, is the covert action of recording the keys struck on a keyboard, typically without the user's knowledge or consent. This can be done through software programs, hardware devices, or even malicious code embedded in websites or applications.
How It Works
Installation: Keyloggers are installed on a device through various means, such as:
Software Installation: Malicious software can be installed through phishing emails, infected websites, or bundled with other software.
Hardware Installation: Physical devices can be attached to keyboards or embedded within them.
Remote Access: Attackers can install keyloggers remotely through security vulnerabilities or social engineering techniques.
Keystroke Recording: Once installed, the keylogger discreetly records every keystroke made on the keyboard, including:
Passwords
Personal information
Credit card numbers
Email content
Chat conversations
Search queries
Online banking details
Data Transmission: The recorded keystrokes are then transmitted to the attacker, either:
Locally: Stored on the device for later retrieval.
Remotely: Sent over the internet to the attacker's server.
Purposes of Keylogging
Cybercrime: Stealing sensitive information for financial gain, identity theft, or espionage.
Surveillance: Monitoring employees, children, or spouses without their consent.
Password Theft: Capturing passwords to gain unauthorized access to accounts.
Data Collection: Gathering information for targeted advertising or market research.
Risks and Consequences
Privacy Violation: Keylogging can compromise sensitive personal information, leading to identity theft, financial fraud, blackmail, or reputational damage.
Security Breaches: Stolen credentials can be used to access corporate networks, bank accounts, email accounts, or social media profiles.
Reputational Damage: Keylogging scandals can tarnish the reputation of individuals and organizations.
Prevention Tips
Be Cautious Online: Avoid clicking on suspicious links or attachments, and only download software from trusted sources.
Keep Software Updated: Install security patches and updates regularly to address vulnerabilities.
Use Strong Passwords: Create unique and complex passwords for all accounts, and change them regularly.
Install Security Software: Use reputable antivirus and anti-malware software with keylogger detection capabilities.
Be Aware of Physical Access: Secure your devices and be mindful of who has physical access to them.
Use Two-Factor Authentication: Add an extra layer of security to your accounts, especially those containing sensitive information.
Check for Keyloggers: Regularly scan your device for keyloggers using reputable security tools.
Be Vigilant: Be cautious about what you type, especially when using public computers or untrusted networks.
M
Malware
Malware, short for malicious software, is any software intentionally designed to cause harm to a computer system, network, or device. It encompasses a wide range of threats, including viruses, worms, Trojans, spyware, ransomware, adware, and more. These programs can infiltrate systems without the user's knowledge or consent, often through deceptive tactics, and execute various harmful actions.
Common Types of Malware
Viruses: Self-replicating programs that attach themselves to other files and spread throughout a system, often corrupting or deleting data.
Worms: Similar to viruses but can spread independently without user interaction, often exploiting vulnerabilities in networks to propagate.
Trojans: Disguise themselves as legitimate software to trick users into installing them, then carry out malicious actions like stealing data or granting remote access to attackers.
Spyware: Secretly gathers information about a user's activity, including keystrokes, browsing history, passwords, and personal data, often without their knowledge.
Ransomware: Encrypts a victim's files and demands a ransom payment in exchange for decryption, holding data hostage.
Adware: Displays unwanted advertisements, often intrusively and excessively, sometimes collecting user data for targeted advertising.
How Malware Spreads
Email attachments: Opening infected attachments can trigger malware installation.
Downloading infected files: Downloading files from untrusted sources can introduce malware.
Visiting malicious websites: Some websites can automatically download malware onto a device.
Using infected USB drives: Plugging in infected USB drives can spread malware.
Exploiting software vulnerabilities: Malware can take advantage of security flaws in software to infect systems.
Social engineering: Attackers may trick users into installing malware through phishing emails or social media scams.
Effects of Malware
Data theft: Stealing sensitive information, including passwords, financial data, and personal files.
System damage: Corrupting or deleting files, slowing down system performance, or even rendering devices unusable.
Identity theft: Using stolen information to commit financial fraud or other crimes.
Financial loss: Incurring costs for data recovery, system repairs, or ransom payments.
Business disruption: Interrupting business operations and causing productivity losses.
Reputational damage: Damaging the reputation of individuals or organizations.
Prevention Tips
Install antivirus and anti-malware software: Keep it updated and run regular scans.
Be cautious online: Avoid clicking on suspicious links or attachments, and only download software from trusted sources.
Keep software updated: Install security patches and updates regularly to address vulnerabilities.
Use strong passwords: Create unique and complex passwords for all accounts, and change them regularly.
Be wary of phishing emails: Don't click on links or open attachments from unknown senders.
Back up your data: Regularly create backups to protect against data loss in case of a malware attack.
Educate yourself and others: Stay informed about malware threats and best practices for staying safe online.
Watch the video to learn more about malware and how it avoid it!
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA), sometimes referred to as two-factor authentication (2FA) or two-step verification, is a security measure that requires users to provide multiple pieces of evidence (factors) to verify their identity before granting access to an account or system. This adds an extra layer of protection beyond a simple username and password, making it more difficult for unauthorized individuals to gain access, even if they have stolen or guessed a password.
Common Factors Used in MFA
Knowledge Factors: Something the user knows, such as:
Password
PIN
Security question answers
Possession Factors: Something the user has, such as:
Smartphone
Security token (e.g., hardware token, software token)
Smart card
Inherence Factors: Something the user is, such as:
Fingerprint
Face scan
Retina scan
Voice recognition
How MFA Works
Initial Login: The user enters their username and password as usual.
Additional Verification: The system prompts the user for a second factor, such as a code from a text message, a security token, or a fingerprint scan.
Factor Validation: The system verifies the additional factor, ensuring it matches the user's registered information.
Access Granted: If both factors are successfully validated, the user is granted access to the account or system.
Benefits of MFA
Enhanced Security: Significantly reduces the risk of unauthorized access, even if passwords are compromised.
Compliance: Meets industry regulations and standards that require stronger authentication measures, such as PCI DSS and HIPAA.
Data Protection: Protects sensitive information and assets from breaches and unauthorized access.
Peace of Mind: Provides users with greater confidence in the security of their accounts and data.
Common MFA Applications
Online banking and financial services
Email accounts
Social media platforms
Cloud storage services
Corporate networks
VPNs
Remote access systems
Recommendations
Enable MFA on all accounts that offer it.
Choose a combination of factors that are both secure and convenient for you.
Keep your authentication factors safe and secure.
Be aware of phishing scams that try to trick you into revealing your authentication factors.
Watch the video to learn more about multi-factor authentication and how it works!
O
Open Source Software (OSS)
Open source software (OSS) is computer software with its source code made available and licensed with the rights to use, study, change, and distribute the software to anyone and for any purpose. This contrasts with proprietary software, where the source code is typically kept secret and controlled by a single entity.
Key Characteristics
Free Availability: The source code is publicly accessible for anyone to download, inspect, and modify.
Distribution Rights: Users can share and redistribute the software with others, often without restrictions.
Modification and Derivation: Users can create modified versions of the software, adapt it to their specific needs, or incorporate parts of it into other projects.
Collaborative Development: OSS development often involves a community of developers working together to improve the software, fix bugs, and add new features.
Transparency: The open nature of the code allows for greater scrutiny and potential for identifying and fixing vulnerabilities.
Common Licenses
GNU General Public License (GPL): Strongly emphasizes open source principles and requires derivative works to also be open source.
MIT License: A permissive license that allows for both commercial and non-commercial use with minimal restrictions.
Apache License: Another permissive license widely used in open source projects, compatible with both proprietary and open source software.
Benefits of Open Source Software
Cost Savings: Often freely available, reducing software acquisition costs.
Flexibility: Customizable to meet specific needs, and users can create their own versions.
Innovation: Encourages collaborative development and sharing of ideas, leading to faster innovation.
Security: The transparency of the code allows for more scrutiny and potential for identifying and fixing vulnerabilities.
Community Support: Often benefits from a large community of users and developers providing support and resources.
Independence: Users are not reliant on a single vendor for updates and support.
Examples of Popular Open Source Software
Operating Systems: Linux, Android, Firefox OS
Web Browsers: Firefox, Chromium
Office Suites: LibreOffice, OpenOffice
Programming Languages: Python, Java, PHP, Ruby
Database Systems: MySQL, PostgreSQL
Content Management Systems: Drupal, WordPress, Joomla
Cloud Computing Platforms: OpenStack, Cloud Foundry
Considerations
Support: While often community-supported, may lack formal support channels found in commercial software.
Integration: Compatibility with existing systems and software can sometimes be a challenge.
Security: While transparency can aid security, open source software can still have vulnerabilities that need to be addressed.
P
Password
A password is a secret string of characters used to authenticate a user's identity and authorize access to a system, device, or resource. It acts as a digital key, ensuring that only authorized individuals can gain entry.
Purposes of Passwords
Protecting Sensitive Information: Prevent unauthorized access to personal data, financial accounts, medical records, proprietary information, and other sensitive data.
Controlling Access: Restrict access to specific systems, devices, applications, or services to authorized users only.
Maintaining Privacy: Protect user privacy by preventing unauthorized individuals from viewing or using their personal information.
Enforcing Security Policies: Enforce compliance with organizational security policies, such as password complexity requirements and regular password changes.
Key Characteristics of Strong Passwords
Length: Longer passwords are generally more secure, ideally at least 12 characters or more.
Complexity: A mix of uppercase and lowercase letters, numbers, and symbols makes passwords harder to crack.
Uniqueness: Avoid using the same password for multiple accounts, as a breach in one could compromise others.
Avoidance of Personal Information: Don't include names, birthdates, addresses, or other easily guessable information in passwords.
Phishing
A deceiving online tactic used to steal sensitive information like passwords, credit card numbers, and personal data. It involves tricking users into believing they're interacting with a legitimate entity (e.g., bank, social media platform, etc.) when, in reality, they're providing information to a cybercriminal.
Think of it like fishing. The attacker, like the fisherman, throws bait (the phishing email, website, or message) to lure unsuspecting victims (the fish) into divulging their valuable information.
Here's how it typically works
Baiting: The attacker sends emails, texts, or messages that appear to be from a trusted source, often using urgency, fear, or excitement to bait the victim. For example, you might receive an email claiming your bank account is frozen or your social media profile is at risk, prompting you to click on a link to fix the issue.
Hooking: The link in the message leads to a fake website or form that looks almost identical to the real one. This can be very convincing, especially if the attacker has cleverly copied the design and logos.
Reeling In: Once the victim enters their information on the fake website or form, the attacker captures it and can use it for various malicious purposes, such as stealing money, taking over accounts, or committing identity theft.
Different types of phishing
Email Phishing: The most common type, using deceptive emails to trick victims.
Spear Phishing: Targeting specific individuals or organizations with personalized messages.
Smishing: Phishing attempts via SMS text messages.
Vishing: Phishing calls posing as legitimate businesses or organizations.
Whaling: Targeting high-profile individuals like CEOs or executives.
How to protect yourself from phishing
Be suspicious: Don't trust unsolicited emails, texts, or messages, even if they seem legitimate.
Hover, don't click: Hover your mouse over links to see the actual destination URL and avoid clicking on suspicious ones.
Check for red flags: Look for grammatical errors, typos, and inconsistencies in the message.
Go directly to the source: If you're unsure about a message, contact the sender directly through a trusted channel like their official website or phone number.
Enable two-factor authentication: Add an extra layer of security to your accounts by requiring a second verification step beyond your password.
Keep software updated: Install security updates and patches regularly to ensure you have the latest protection against phishing attacks.
Report phishing attempts: Report suspicious emails, texts, or messages to the relevant authorities or organizations. Remember, if something seems too good to be true, it probably is. By being cautious and aware of the dangers of phishing, you can help protect yourself from falling victim to these deceptive online scams.
R
Ransomware
Defined: Holding Your Data Hostage
Ransomware is a type of malware that encrypts your files, rendering them inaccessible, and then demands a ransom payment in exchange for the decryption key. It's like a digital padlock on your data, where only the attackers hold the key and you're forced to pay to get it back.
How it works
Infection: Ransomware typically infects your system through phishing emails, malicious websites, or infected software downloads.
Encryption: Once installed, it scans your device and encrypts your files, making them unreadable and unusable. This can include crucial documents, photos, videos, and even entire system files.
Demanding Payment: You'll then receive a message (often displayed on your screen or stored in a text file) explaining your situation and outlining the ransom demands. Payment is usually requested in cryptocurrency like Bitcoin to make it harder to track.
Decryption (Hopefully): If you pay the ransom, the attackers may provide you with a decryption key to unlock your files. However, there's no guarantee they'll keep their word, and even if they do, it can take time to recover your data.
Types of Ransomware
Cryptors: Encrypt your personal files like documents, photos, and videos.
Lockers: Lock you out of your entire device, preventing access to the operating system and all files.
Doxware: Threatens to leak sensitive information if you don't pay the ransom.
Impacts of Ransomware
Data Loss: Loss of access to critical files can disrupt your work, personal life, and even businesses.
Financial Loss: Paying the ransom encourages cybercriminals and doesn't guarantee data recovery.
Reputational Damage: Businesses can suffer reputational damage from data breaches caused by ransomware.
Psychological Stress: Victims often experience fear, anxiety, and frustration while dealing with a ransomware attack.
Prevention Tips
Back up your data regularly: Regularly back up your files to an external storage device or cloud storage to ensure you have a clean copy in case of an attack.
Be cautious online: Avoid clicking on suspicious links or opening attachments from unknown senders.
Keep software updated: Install security updates for your operating system and applications to patch vulnerabilities exploited by ransomware.
Use antivirus and anti-malware software: Employ reputable security software with ransomware protection features.
Be suspicious of unsolicited emails: Watch out for emails with urgent language or threats, especially requests for financial information.
Educate yourself and others: Stay informed about the latest ransomware threats and best practices for staying safe online.
Remember, prevention is key. By taking precautions and having proper backups, you can significantly reduce the risk of falling victim to ransomware and minimize its impact if it does happen.
S
Social media
Social media is a broad term encompassing online platforms that facilitate the creation, sharing, and exchange of content, ideas, interests, and other forms of expression through virtual communities and networks. Essentially, it's like a giant digital hangout where people connect, communicate, and engage with each other in various ways.
Here are some key characteristics of social media:
Interactivity: Users can actively participate by creating and sharing content, commenting on others' posts, and interacting with each other.
Community Building: Platforms enable users to connect with friends, family, colleagues, and like-minded individuals, forming online communities centered around shared interests.
Content Sharing: Users can share various types of content, including text, photos, videos, music, and live streams.
Information Dissemination: News, updates, and information spread quickly through social media channels, often influencing public opinion and trends.
Personal Branding: Individuals and businesses can build their online presence and personal brand through social media engagement.
Marketing and Advertising: Businesses can use social media platforms to reach target audiences, promote products and services, and engage in social marketing.
Common types of social media platforms
Social networks: Focus on connecting people and building relationships (e.g., Facebook, Instagram, Twitter).
Media-sharing networks: Primarily for sharing and consuming visual content (e.g., YouTube, TikTok, Pinterest).
Microblogging: Platforms for publishing short, text-based updates (e.g., Twitter, Mastodon).
Forums and message boards: Online communities for discussions and information sharing on specific topics (e.g., Reddit, Quora).
Professional networking: Platforms for building professional connections and career opportunities (e.g., LinkedIn).
Social media has significantly impacted our lives
Communication: Changed how we connect and communicate with others, both locally and globally.
Information Access: Increased access to news, information, and diverse perspectives.
Entertainment: Offered new forms of entertainment and content consumption.
Business and Marketing: Transformed marketing and advertising, allowing businesses to reach wider audiences.
Social and Political Movements: Played a role in mobilizing social and political movements and spreading awareness.
However, social media also comes with challenges
Misinformation and echo chambers: The spread of fake news and information silos can limit exposure to diverse viewpoints.
Privacy concerns: Sharing personal information online raises concerns about data privacy and security.
Addiction and mental health: Excessive use can lead to addiction and negative impacts on mental health.
Cyberbullying and harassment: Online platforms can facilitate cyberbullying and harassment towards individuals.
Social media is a powerful tool with both positive and negative aspects. It's crucial to be aware of its potential benefits and risks to use it responsibly and safely. By being mindful of our online behavior, protecting our privacy, and consuming information critically, we can maximize the positive impacts of social media in our lives.
U
URL
URL stands for Uniform Resource Locator. It's essentially the address of a specific resource on the internet, like a website, image, or document. It's like the street address for your house in the digital world, telling your device where to find the information you're looking for.
Here are the key components of a URL
Protocol: This tells your browser how to access the resource. For example, http is the most common protocol for web pages, while ftp is used for file transfers.
Domain name: This is the human-readable name of the website or server hosting the resource. It's like the street name for your house.
Path: This specifies the location of the resource within the website. It's like the house number and room number inside your building.
Query string: This is optional and contains additional information about the resource, often used for searches and forms. It's like specific instructions for finding a particular room or item within your house.
Fragment identifier: This is also optional and points to a specific part of the resource, such as a heading or section. It's like a bookmark within the document.
V
VPN
VPN stands for Virtual Private Network. It's a secure tunnel that encrypts your internet traffic, making it private and anonymous, even when using public Wi-Fi networks. Think of it as a secret, protected passageway that shields your online activities from prying eyes.
Here's how it works
Connecting to a VPN Server: When you activate a VPN, your device establishes an encrypted connection to a VPN server, which acts as a secure gateway between you and the internet.
Data Encryption: All the data you send and receive, including your browsing activity, downloads, and online communications, is encrypted before it leaves your device. This means it's scrambled and unreadable to anyone who might intercept it, such as your internet service provider, hackers, or government agencies.
IP Address Masking: The VPN server assigns you a new IP address, which masks your actual IP address and location. This makes it harder for websites, trackers, and advertisers to identify you and track your online activities.
Secure Tunnel: Your encrypted data travels through this secure tunnel to the VPN server, which then forwards it to the intended website or online service. The website sees the VPN server's IP address, not your actual one, protecting your privacy.
Data Decryption: When the website's response comes back, the VPN server decrypts it and sends it back to your device through the secure tunnel.
Key Benefits of Using a VPN
Privacy Protection: Prevents your internet activity from being monitored or tracked by your ISP, government agencies, or third-party websites.
Security: Protects your data from hackers and snoopers, especially on public Wi-Fi networks.
Access to Geo-Restricted Content: Allows you to bypass geographical restrictions and access websites, streaming services, and content that might be blocked in your location.
Online Anonymity: Masks your IP address and location, making it harder to track your online activities.
Secure Remote Access: Enables you to securely access work or home networks remotely, even when using public Wi-Fi.
Common Uses of VPNs
Protecting privacy while browsing the web, streaming content, or using online services.
Securing online transactions and banking activities.
Accessing geo-restricted content like streaming services or websites blocked in certain regions.
Bypassing censorship and internet restrictions in some countries.
Safely using public Wi-Fi networks without compromising security.
Remotely accessing work or home networks for secure file sharing and collaboration.
W
Want More Insights?
Don't see a term you think should be in our Encyclopedia? Use the "Contact us" form to submit your suggestion.
Learn about our goals and how you can work with us to help accomplish them!
Use this tool from PCRD (Purdue Center for Regional Development) to learn more about each county's digital barriers.
Acronyms are frequently used in a lot of sectors, but especially with government. Use this dictionary to learn what all those letters mean.
